Editor’s note: This text-based course is an edited transcript of the webinar, Everyday Cybersecurity Best Practices for Respiratory, presented by Josiah Dykstra, PhD.
Learning Outcomes
After this course, participants will be able to:
- Identify common markings of scam emails and websites.
- Explain the attributes of strong passwords
- List three ways to ensure confidentiality of protected health information
RTs Are Immersed in Technology
It is a pleasure to be here to talk about best cybersecurity practices. I think these things will apply whatever your role is as a human, but we are primarily going to talk today about the needs in healthcare. This is not a HIPAA talk per se, but many of the things we will cover address required HIPAA rules. It is a way for you to approach your everyday interactions in the healthcare setting, knowing that they also contribute to essential healthcare protections. This is a site I think we have become very accustomed to during the pandemic and a site that you probably were familiar with within healthcare for much longer than that. My wife is an audiologist and teaches me a lot about healthcare, the needs in cybersecurity, and the protections that you all, as healthcare providers, use to protect your physical health.
We cannot cover everything, but we will talk about the prevalence of malicious emails and websites because that leads to many infections. A significant percentage of bad things that happen on the internet begin with a malicious email. I wanted to help you understand what does that looks like and how to avoid that. We are going to touch a little bit on password best practices. This tends to be the one that people get the most training about, but I want to give you a little different perspective about how attackers think about this to get into the mind of an attacker to help you be safer and more secure.
Everyday Best Practices
- Avoiding Malicious Email and Websites
- Password Best Practices
- Smartphone Best Practices
- Protecting Sensitive Data
I am going to give you three best practices for smartphone cybersecurity because I think it impacts our professional lives. Whether you have a personal phone or an employer's phone, both of those do matter. Smartphone security is important if you check your email, work email, or schedule, even on a personal device. I will give you three concrete things that you can do. We will also talk about how to protect sensitive data, mostly protected health information, and any data that does not fall specifically into that realm as defined by the law but also wants to keep safe. The last thing, which is not an everyday cybersecurity best practice, but I think will apply to you more and more going forward that we will touch on at the end, is telehealth.
I will give you some advice on things to think about and make sure your telehealth offerings are as secure as possible. Cybersecurity is often, I think, visualize something like this, which is fear-mongering. It seems like people, such as myself, who talk about cyber threats talk about the bad things. There are attackers out to get us, and all of our information is at risk, and the world will end. I think that is an unhelpful way to talk about cybersecurity. I want to help you understand the real levels of threats, but based on evidence, not just fear. I do not think that helps anybody from your home setting to your professional setting make better choices
Common Misconceptions
- We have a firewall. Our data is protected
- Nobody can figure out my password
- I will know if my computer is infected
- Cybersecurity is expensive and difficult to use
- Compliance is a sufficient security strategy
It is not to think about cybersecurity as fear, but as I said, to help make sure that your job can be done securely, so it is not meant to be fear-mongering. Let me also say that there are quite a few misconceptions that I hear as a professional. I think people pick up these myths from a lack of knowledge or just common misunderstandings. Sometimes it is poor training. I will try to dispel as many as I can as we go along. These myths can be quite dangerous, in any case. If, for example, somebody in your organization says cyber security does not matter to me, we are too small. We have a private practice of two people, we will never be attacked, or I will know, it will be evident to me when my computer is attacked.
All About Hackers
We are all relatively similar likelihood of victimization. Attackers care very little about you as an individual or your business specifically. They go after targets, almost opportunistically. They can send out millions and millions of fake emails without really caring who gets them as long as some victims click on the link and get infected. We also underestimate our risks sometimes about how likely it is that an attacker can figure out our passwords. We will talk later about passwords, but you should always assume that an attacker can figure out your password and have other mitigations in place, even if that happens. Let me spend just a couple of moments talking about attackers. I have spent a long time studying and trying to understand the humans who make computer crime cyber attacks, and the closest analogy to explaining this is this picture in Figure 1.

Figure 1. Picture of poke player.
Why do people play poker? Lots of reasons, I presume. Some people play just for fun and for entertainment, some play for the challenge of it because it is interesting and mentally challenging for them. Some play for the money. Some even play as a livelihood. That is how they make their money. They are obsessed and have an addiction.
For the same reason, I think people also engage in malicious cyber activity in hacking. Some people do it for fun, some do it for the challenge, and others do it for money. There are all kinds of hackers worldwide, not just governments or teenagers in their basement wasting their time.
Yes, some teenagers hack, and yes, governments spy on other governments. However, there are criminal enterprises out there whose job is to do things like ransomware. They have a business structure, and they have customer service, and because the money matters to those kinds of criminals too. There is a vast range of motivation for why people do this kind of activity. Healthcare does attract criminals because it is more valuable. What I mean by that is, if a criminal steals your credit card number, if they want to try and sell your credit card number to a buyer on the black market, that credit card number, probably somebody will pay like $5 for a good credit card number.
On the other hand, a healthcare record can get as much as $250 per record on the black market. Moreover, that healthcare record is so valuable because of the rich information it contains for a criminal. Social security numbers, maybe payment information, and other personal information can lead to identity theft. The criminal can make more money by exploiting the healthcare record even much more than a credit card. The reason that there are many rules and regulations about protecting health information is that hackers go after that information, and it needs protection even more than average. The kinds of cybersecurity you have at home, commensurate with the risks you have in your home. But the rules and regulations and the mandatory cybersecurity in healthcare are reasons why it is more significant because of the risks.
Hacker Mindset
- Phishing: Trick the user to give information or take a dangerous action
- Websites: Trick the user to give information or take a dangerous action
- Attachments: Malicious files infect the computer
- Passwords: A "key" to one or many sources of data or trust relationships
- Remote Attack: Hacks against internet-facing machines
Let's talk about a few ways that hackers go about their malicious business. One is phishing, which is the most common technique that hackers use to try and get access to your account or your computer. Phishing is just a way to trick the user into giving up information or taking some dangerous action. A phishing email might include an attachment, like a file or a link to a website that is just not legitimate. It looks like your bank, EHR, or your human resources department, but the attacker is trying to trick you, exploiting your human weaknesses to try and do something malicious. Phishing is very, very common.
Phishing is also how other kinds of attacks get into computers. Ransomware sometimes comes after somebody has been tricked with a phishing email into downloading a ransomware file. Similar to phishing emails are malicious websites. An attacker might set up a website that looks like your legitimate email. They can copy every picture. It looks the same, except for some red flags that would otherwise tell you, you know what, this probably is not my email provider. But if you are busy, distracted, not thinking, or not paying attention to those red flags, that is how attackers get people to fill in their username and password. The attacker has the information through this malicious website.
There are lots of malicious websites on the internet. The cybersecurity community is always playing whack-a-mole, chasing down malicious websites and getting them taken down or blocked. It is a cat and mouse game because the attackers set up a new one the next day. In addition to links are malicious attachments, and you should be very careful about opening an attachment in an email that you did not expect, even if it seems like it could be from somebody you know. That's the tricky thing that requires some careful thinking. It might be a Word document that looks like a patient's medical history, or it might look like an invoice for something you purchased online.
When you open that document, a hacker can have malicious code also run at the same time to infect your computer. So an antivirus program is one way to help detect those malicious attachments, but it still relies upon us as humans to be cautious not to open attachments that may be malicious. Passwords are a powerful technique for an attacker. If they can get access to your password, that opens up a goldmine of information for them. One reason this is so dangerous is that people reuse passwords. Every time you use a common password, it is an opportunity for a hacker to get that password, and then they are just going to go try that password on every site they know of on the internet.
If they capture it, for example, in an airport and you have logged into your email, they are going to almost immediately take the password that they have stolen and try to log into Netflix and Amazon and every retailer, believing because it is true that many people reuse that password. The attacker gets access to unlocking information. We will talk more about mitigations for this later in the presentation. I want to mention that the last one is remote attacking because this is what people generally think hackers do. They sit somewhere remote across the internet, maybe in another country, and launch cyberattacks like missiles towards your computer. It is very uncommon. Modern computers are pretty good at blocking this kind of attack, and it is not very prevalent. Most attacks do not work like that. Attackers might be far away, but generally, they're trying to send you fake emails or set up those fake websites. The remote attack just against your computer with no interaction is very uncommon.
How to Arm Yourself
At a high level, what are some things that you can do? One, you can help arm yourself by having some healthy skepticism. I am not saying that you should be fearful of every email you get from now on, but maybe spend one or two extra seconds thinking, did I expect this? Could this be malicious? Even though those one or two extra seconds will prevent you from a lot of fake emails, a little bit of healthy skepticism can go a long way. Number two is to get evidence-based advice. Many people want to provide cybersecurity information, and knowing whom you can trust is difficult. These are three organizations that I feel very comfortable providing reputable, validated evidence in cyber security. The National Institute of Standards and Technology (NIST), Homeland Security (CISA), and the British cybersecurity organization called the National Cybersecurity Center. They all publish information on their website, they all have Twitter accounts, on Facebook groups, and if they say there is a crisis, you should believe them. For example, Homeland Security reminded people that Apple put out a new update for iPhones this week and said, this is very dangerous. You should update this right away. That is one source of information that you should pay attention to.
I cannot vouch for every cybersecurity expert on the planet, but make sure the advice that you get is true. Continuing education is essential, and just like in your professional life, because technology changes so often, even how we authenticate on our phones has changed. We will talk about the move from passwords to facial recognition, for example. That is of a relatively modern advance, and so too is ransomware. When ransomware first appeared, people did not understand how it got on my computer and how I got it off? There is some continual education about the threats and the most effective cybersecurity countermeasures. The last thing is sort of tongue in cheek, which is, there are no special snowflakes. Everybody thinks that their situation is unique or that you know what. I understand that many people get phishing, but not me. I would never be targeted, or why would an attacker ever go after me? I'll be okay. I am here to tell you that this is not true. Hackers go after us all. We all need similar kinds of protection. We should not believe that our circumstances are special for any reason.
Avoiding Malicious Email and Websites
Let's dive into malicious emails and websites. How do attackers get in? Lots of ways. Some are pop-ups on web browsing. You have probably seen this many times when you go to a website, and suddenly, it is popping up with advertisements, some of which even look like legitimate alerts from your antivirus. When a user clicks on that pop-up, that is one way a computer can become exploited. Another is that the user runs a malicious file that they think is benign. They want to install a game or install a new application, and without knowing, sometimes that application also allows a hacker to get in. That is a second way that hackers get on. A third is stealing and reusing usernames and passwords.
If they can get that information, they do not need to bother you anymore. Hackers can go to their computer and log into your health system, email, or bank simply using your credentials. A lot of people ask me, what do hackers even want with my computer? There are a couple of things. Money certainly is one. As we talked about, the amount of money they can get from a credit card pales compared to a health record. Sometimes, those attackers are going after specific data like that, like credit card numbers or health records. On the other hand, the hacker wants to exploit your computer to attack other computers.
You might not even know that this is happening, but once the attacker can run programs on your computer, they will use it to send a malicious email that originated from your computer on your network. They are taking advantage of that system for a different reason than money, but money is significant. Indeed, if you can imagine if you were a criminal, that would be a strong motivator.
Responding to Scams
What should you do? Imagine you are in a situation where you have some red flags that go off, you have had this healthy skepticism and think you know what, this email might be a scam. It looks like it might be fake. What should you do? My first bit of advice is not to respond. Do not write them back and say, please remove me from this email list. That only confirms to the attacker that the email works and that you read it, so do not respond. Instead of just clicking delete, number two is to report that message as spam or phishing either to your security staff at your employer or in your healthcare setting. Some email providers have this built-in button. For example, in Office 365, you can say, I would like to report this as spam. The nice benefit of that is you help protect everybody who got that message because it teaches the system, and it tells Microsoft this is a fake message, and they can start to block it for other users.
Another way to prevent getting these kinds of messages is to limit how many times you give away your email. If every time you fill out a form or register for a conference, every time you give away your email address is another opportunity, not only for annoying marketing, but it is an opportunity for your email address to fall into the hands of scammers. Use care with the number of people that you give your email to. As I mentioned, be skeptical about the links and attachments you get and spend a little extra time deciding whether you believe it to be legitimate before you open it.
The answer is not to open the attachment and then decide that it is too late. You have to decide before you open it. As I mentioned, having layered protection is an excellent way to give you backup confidence that a cybersecurity mechanism can protect you even if something goes wrong. In addition to your healthy skepticism, antivirus always running on your computer is another mechanism to detect that something has gone wrong. What about scan websites? If you believe you were browsing the internet and you have landed on a site that seems suspicious, what should you do? My best advice here is to digitally walk away, close that tab, go somewhere else, do not even stay on that website if it seems shady.
If you believe that you have submitted a form with information like your password, that happens, there are still things that you can do, and the world has not ended. The first thing to do is to change that password for the legitimate site. If you went to a site that looks like your email, and then you got suspicious afterward, immediately go and change your email password. You do not want the attacker to be able to use it, even if they captured it accidentally. The last thing is, if you even visit a site that seems a little bit suspicious, make sure to scan your computer for viruses. There is minimal cost to that. The antivirus should be running all the time and should be updated, but you can often manually click a button that says, please scan it right now.
Anatomy of a Phishing Email
Let me point out some of these tricks so that you can know what to look for. Again, as I mentioned, the phishing email tricks you into giving information or taking dangerous action. It is effortless for an attacker to create an email address. They can even create the part that goes after the @ sign. It might look like this one in Figure 2, trying to pretend to be PayPal. The attackers are doing a couple of things in this email. First is a sense of urgency. You can see in big, bold letters that your account is limited.
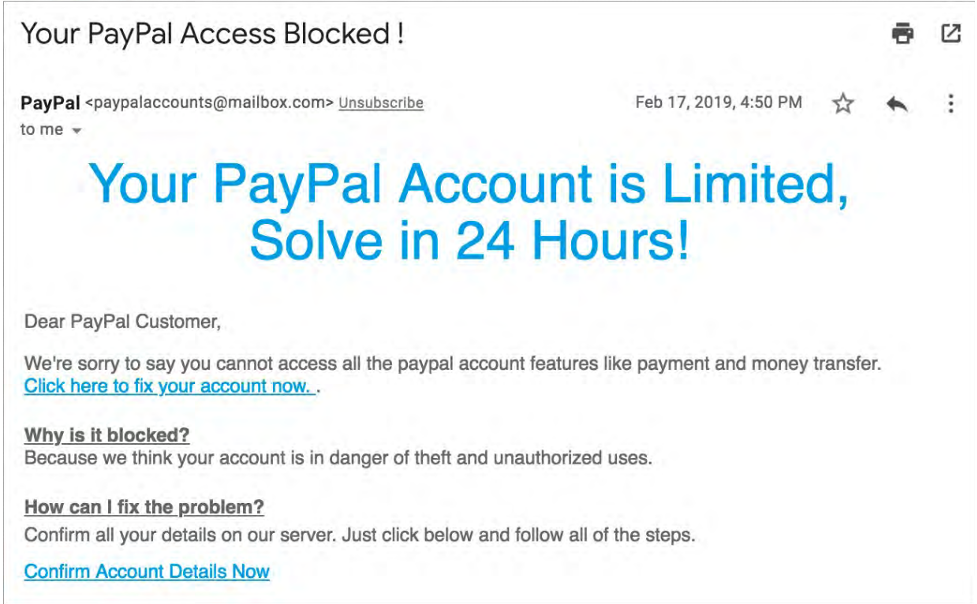
Figure 2. Anatomy of a phishing email.
If you do not take action in 24 hours, something terrible is going to happen. They are appealing to that urgency that you will not slowly think about the problem. You will click on the link without even giving it a second thought. That sense of urgency should already raise a red flag. The second is to look at that email address and decide would the real PayPal send me an email from that address? In Figure 2, it says paypalaccounts@mailbox.com. That is a bit suspicious, and you would expect that a company would send an email from their domain @paypal.com, which should also raise a red flag. Another one is a sort of generic wording or even poor language.
The attackers do not care about whether their English is good because people going to fall for the attack would overlook that. They are trying to go after people who are not going to pay attention. If you notice this says, "Dear Customer," as opposed to "Dear Dr. Smith" or "Dear Jane," that would raise another red flag for me. I would point out the links you see do not show you the URL (Figure 2). It does not say https://www.paypal.com. It has a link that says, click here to fix your account. What they are doing is hiding from you where that will go on the internet. For example, if you click that link, it might take you to a website that looks like this below in Figure 3.
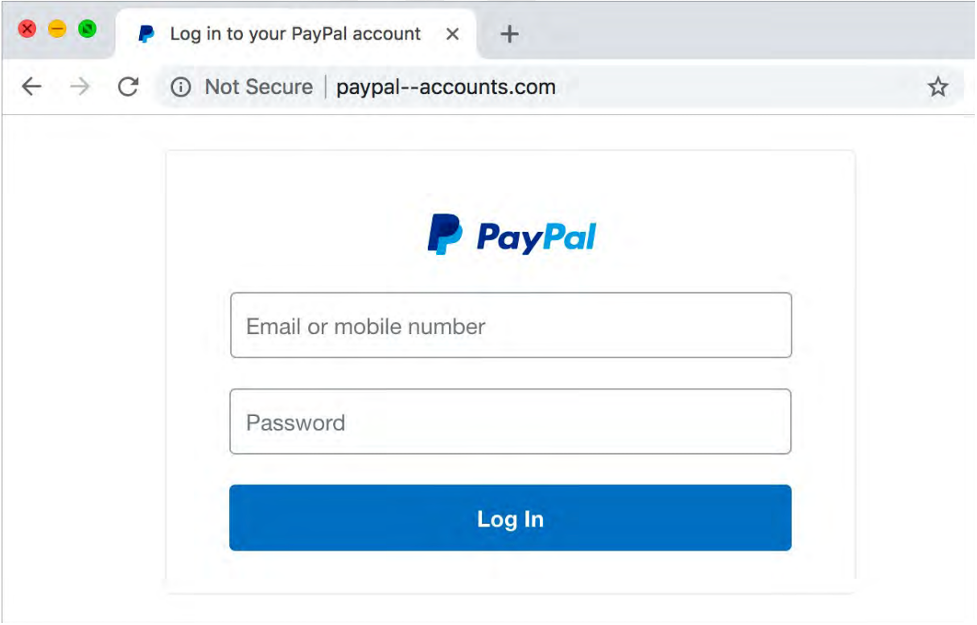
Figure 3. Anatomy of a phishing website.
It is easy for a hacker to copy legitimate web pages and make them look identical to the actual one. I took this screenshot (Figure 3) of what the PayPal login looks like. Now, it would be impossible to know that this was fake. The way to tell is to look at the URL in the address bar. It says not secure paypal--accounts.com. That is the telltale sign that this is not the actual PayPal. When I see this, it is time to walk away. Thus in the worst case, visiting the wrong website can attempt to exploit your computer by looking at this website.
The best case is that you close this browser, and nothing terrible happens. You can even type paypal.com directly and go to the actual site. If they sent you an email, logging into your real account should also give you the same information. If there is a problem, when you log in, the actual website will tell you. The best advice, close the browser. If you accidentally fill in the form, immediately go and change it. In this case, your PayPal password so that the attackers cannot make use of it. Look for, especially those addresses in the address bar. That is the way to tell.
More Ways to Protect Yourself
Some final ways to protect yourself when receiving a phishing email. One of them is not to click any links in an email. You can always type the address of the place you believe you are going to in a browser. The attackers pretend to be a site, such as a bank, email, or social media account. Go to those websites on your own, do not click the link in the email. That could be a bad day. Another technique is to hold or hover your mouse over a link to see where it will take you.
Let me show you an example of this in Figure 4. The words that appear in the email are not the computer code that sends your computer somewhere on the internet. I just put my mouse over the link, and it tells me where it will take me. In this case, it says it is going to continued.com, but it is going to my website, and somebody who clicks that link would go to my site and not continue. Holding your mouse over any link on the internet will almost always tell you, this is where it will take you. If those two things do not match, that is a red flag, and you should not click that link.
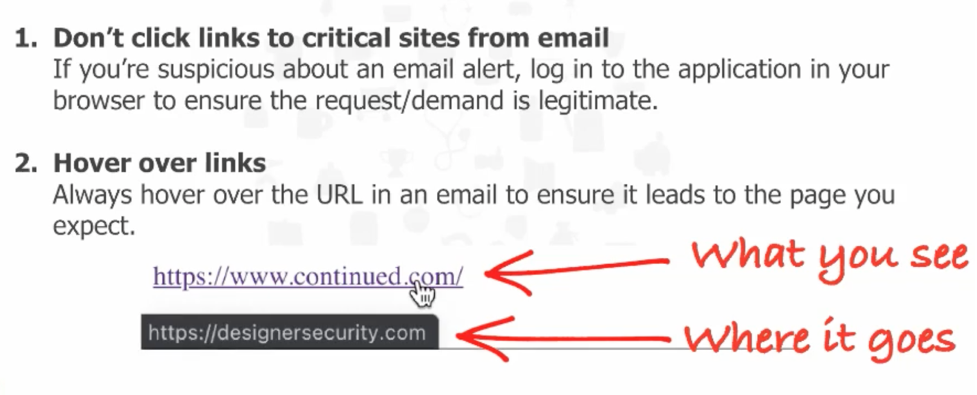
Figure 4. Example of a phishing email link.
Password Best Practices
Let's move on to password best practices because this goes right along with the malicious emails and websites that we saw. There are many ways hackers get passwords, and it is not just you filling in a bad website on the internet, although that certainly is one. The first thing hackers do is guess common passwords. You can go on various websites on the internet and get the most common passwords. Wikipedia has a list of the ten most common passwords for the last ten years, and not surprisingly, the exact words appear all the time.
Second, they do something called "brute-forcing," which is to try every possible combination of characters. They might put your email address in and then try the password, abc123, the password, I love you, and then the password, sunshine. Hackers use brute force to try and use all of those common passwords knowing that many people have them. Now, this is not a very efficient way for an attacker to learn a password, and if the website locks out the account after three wrong passwords, the hackers will not be very successful. If they have a long time and care, they will try your username and letter A. If that does not work, they will try the letter B and then the letter C. They will do this by constructing passwords for ten characters, maybe, 10 A's and then 9 A's and a B, and then 9 A's and a C.
Third, hackers use something called "stuffing." Stuffing is a technique where they use the password, they have captured for one site and try it on every other website. People who reuse passwords are unfortunate, as the hackers are successful with this dangerous technique.
A fourth way that hackers get passwords is by having malicious software running on your computer. They do this with "key loggers." Every button you press on your computer, if the attacker has malicious software running, they can capture all of the keystrokes, including when you type your password. We want to keep malicious software off our computers for this reason as well.
We have already talked about the last one, which is phishing, tricking users into giving away their passwords. The hackers do not need to guess if you give it to them. They try to trick you for that reason.
“Strong Passwords”
Strength Meters look at:
- Length
- Patterns (dictionary words, patterns, repeats, …)
- Characters (letters, numbers, capitalization, …)
- Your password history*
National Institute of Standards and Technology (NIST):
- Special Publication 800-63B
- Updated June 2017
- Widely accepted (adoption lagging for new guidance)
- No more password expirations or mandatory change
- “Easy to remember, hard to guess
- https://correcthorsebatterystaple.net/
Password strength meters have become very common on the internet to help users understand if they have picked a good password. The strength meter uses an algorithm, looks at the mixture of numbers and letters and characters, and shows you in red, yellow, green whether it thinks that the password you have chosen for a new website is strong or not. It is not perfect, but it certainly is helpful to the user in real-time know that the password they picked is not good enough, may need to add more characters. Those strength meters look at a couple of things. They look at the number of characters. Some of them even know what your prior passwords were.
For example, if the bank says you have to change your password right now, some password strength meters will say you cannot use your current password or the last ten passwords you have. Windows computers are pretty notorious for this. There are, unfortunately, lots of bad advice about passwords. For example, NIST put out password guidance that many people implement, including the government and healthcare organizations. However, they changed their guidance in 2017, even though many policies and procedures at businesses have not been updated accordingly. If your employer says you have to change your password every month, every quarter, or once a year, that is bad advice. You could point them to the NIST website and say that government recommendations do not change passwords that often. The government stopped giving that advice. They essentially said you should pick passwords that are number one, easy to remember, and two, challenging for a hacker to guess.
What did they mean by that? There is a very common technique for this: picking three or four random words meaningful to you but would be very difficult for a hacker to figure out. Your password might be the phrase, zebra cart slick Monday, and maybe that has some special meaning to you, but it is a powerful password. It does not have any numbers or special characters other than spaces, but it is just as strong as the one right beneath it. You can go to the website, which is four random words called CorrectHorseBatteryStaple.net, and it will help you generate four-word passwords.
The last is a password that looks like random gobbledygook, WvPM3$7kF@x#J5laP. I could never remember that. My memory is not that good, but I have passwords that look like that because I use password manager software. The software that I run on my computer remembers a different, random password for every website I use on the internet. It has hundreds and hundreds of them. When I log into a site like Facebook, it shows here. The password manager says you do not have to know what your password is. We will fill that in for you. I only have to remember one single password to unlock this vault of all of my passwords. You can have very long 20 or 30 character passwords for sites like Facebook or your email that you do not have to remember. Password managers are an excellent opportunity for your home computers and, hopefully, your work setting.
As I mentioned, I am a big fan of more usable security, and things like facial recognition and fingerprints are becoming a new way to authenticate. Instead of typing in any passwords, the computer looks at your face or some other way that knows that you are the right person to log in. I think this is especially helpful in healthcare, where the time it takes to log into a computer might be a life-or-death delay. I do not want computers to remain unlocked all the time, and I do not want people to share their passwords. I am a big fan of research to push new technologies that allow people to walk up and securely authenticate to that computer with as little work as possible.
Smartphone Best Practices
Top 3 Best Practices
- Set a Screen Lock Password
- Encrypt Your Phone
- Enable “Find My Device/Phone”
The smartphone in your hands has access to a tremendous amount of information. It is the portal to all kinds of things on the internet. It probably automatically downloads your email and knows who all your contacts are. It might have private photos of your family, your children, and maybe it also has access to your work, including health records. We need to protect our devices because the information exists, and the risk is high. The likelihood that a desktop computer will get stolen pales compared to the number of smartphones that are just accidentally left in coffee shops or fall out of our pocket or purse. Lost devices are incredibly common, and it is a threat to all the information on that device.
If you walk away from your laptop or your phone, that is an opportunity for somebody to walk by and steal it. The prime reason is that mobility, or the very thing that we love about mobile devices, is also the biggest threat. What can you do to help protect that? The first thing that I recommend is to set a password. If you can pick up your phone and it automatically unlocks, a criminal could do the same thing. You want to deter somebody who steals that device, making it difficult for them to access the information. Make sure the screen automatically locks and make sure that you have set a pin, a face ID, a fingerprint, anything that is required to get on there. Here's a link, https://designersecurity.com/SmartphoneSecurity if you want more tips like this. I have ten total, including videos. I walked through Android and iPhone, what buttons to touch, and how to enable these settings. If you want to watch those videos after this presentation, please feel free.
The next thing that I recommend in my top three for smartphones is to encrypt your phone. Encryption means that it scrambles all of the data on the phone, so if a criminal gets access to the phone and the power is off, if they tried to read the hard drive in the phone, it would look garbled. Once you enable encryption on your device, that is it. You never have to enter the password again, it does not slow the phone down, and it is automatically turned on for iPhones and Android. It is easy to set up. It protects that device if it is lost or stolen, attackers or anybody else cannot get the information off.
The third thing that best protects health information and confidential data on your phone is to turn on a feature that exists on all modern smartphones to find a lost device. Even if you leave it in an Uber or it falls out of your bag, Find My Device does two things. One, it might allow you to get the device back. If it got turned into the barista at the coffee shop, and if you go on this website to find my iPhone or find my Android, you can go back and immediately get the device. If that is not possible, you can remotely erase all of the data. If that phone cannot be recovered or a criminal stole it, you do not want them to have any access to it. Thus, you can go on the website after you learn that it has been lost, and you can say, all right, I do not think I will ever get this back. Please erase all of the data. Some companies have this feature turned on because they also want to protect the information on your device. The remote wipe, the remote delete is one way to protect the opportunity for protected health information to get out.
When it audits a data breach, the government says that we have to assume that any information on that phone was a data breach unless you can prove that you implemented cyber security to protect against it. You can show protection so that it is not a data breach by saying that we have remote wipe turned on and remotely erased the devices. That will help HHS feel much more comfortable that there was no data breach, and it can prevent even things like fines.
Protecting Sensitive Data
How do we protect sensitive information? We have talked about a couple of practical ways like email protection and smartphones. How else do we protect access to the information? In cybersecurity, we talk about three ways of developing technology that helps do this. We are interested in protecting against unauthorized access, changes, and disruption to your protected health information or other sensitive information. We call these confidentiality, integrity, and availability. These are provided by lots of the cybersecurity mechanisms we already talked about.
Passwords are one example of authentication. It is a way to help protect the confidentiality of files on your device. It is a different kind of protection than encryption, which scrambles the data. The password means that only the person who knows the password can get access. You are authenticated and allowed to see it. We do all of them because they work together to ensure that you are allowed to see it, and yes, the file cannot be changed by an unauthorized person. Somebody can delete that file accidentally. We want to make sure that we protect all three things: access, changes, and disruption.
What Can They See and Touch?
Many people in healthcare do not think about it quite as often because the sensitivity of data is sometimes literally showing on the screen. The health information, medical records, or testing results, or other instrumentation are right on the screen for anybody who can see that screen. In a doctor's office, I tell people, turn the screen so that patients in the waiting room cannot see what is on the screen. That is mitigation to help protect that information. If you are taking photos, turn off the screen in the photos. I cannot tell you how many times I have seen healthcare practices on social media trying to advertise their staff sitting in an office, and I can read a medical record on the screen. That is pretty dangerous, and the physical world is part of HIPAA protection. We need to make sure that patients cannot touch the printer or cannot unplug the keyboard. All of that should be out of arm's reach, along with what people can see on the screen at any given moment.
Secure Communication
- Most to Least Secure:
- United States Postal Office
- Patient Portal
- Text Message
There are some misconceptions about secure communication, and I want to talk about that for a moment. There are different levels of security in the communications that we send. You might send even protected health information through the mail, or you use a patient portal, or on the other spectrum, maybe you want to text with a patient or email with a patient. On the spectrum, the US Postal Services is the most secure of all of these. It has the most protections in place and the most counter-measures to protect information. Email is the least secure of all of these. The way that I described email is a little bit like a postcard. When you send a postcard through the mail, anybody who sees the postcard can read the communications. Email is precisely the same way. Email, as it travels around the internet, is not protected. Anybody who can see the email can read the communication.
Let's talk about this in a digital sense. On one side is you and your computer, and you are trying to communicate with a colleague or a patient over the internet. In some sense, the internet is an abstraction. It is just a big cloud, and as long as the information moves around, it works. When you pick up the telephone, I do not care how the telephone system works as long as the other person I want to talk to answers the telephone. Your communication, like email, moves around to lots and lots of computers around the internet. The attacker, for example, might be sitting in your patient's home network, an infected device that you have no control over.
The postcard or the email that travels around the internet to your patient, the attacker can read, which is why it is so insecure. There is no such thing as secure email. It just does not exist. The closest thing that we can do is encryption. When we use a portal or a patient portal, they have to log into a secure website on the internet. You are inputting the information, and the other party or the patient can receive that information that is encrypted along every route. No matter where the hacker is, it looks like scrambled information that they cannot read if they go to a secure website. Companies who offer secure email are doing this portal version, where they send a link to a website. I am totally fine with that, and I love patient portals. I think that is a secure and effective way to communicate.
What is Encryption Anyway?
I think a lot of people do not understand the technical details of encryption. It is not important. The general technique, though, is that you have a key, just like a physical key to your house or office, that turns human-readable text not into garbage but into muddled data that is not intelligible. Then you can use a key also to turn it back into text that somebody can read. The protection of those keys allows us to send that middle file that is not readable around the internet and has confidence that other people do not have the key to read it.
Security Considerations for Telehealth
COVID-19 Relaxations
In 2020, the U.S. Department of Health and Human Services (HHS) relaxed its enforcement of HIPAA and telehealth regulations to enable health care providers to use telehealth more readily during the COVID-19 public health emergency. You can read this notification document in detail at the HHS website - it is entitled Notification of Enforcement Discretion for Telehealth Remote Communications During the COVID-19 Nationwide Public Health Emergency. This notification remains in effect until the COVID-19 national emergency is declared over. At that time, these relaxations go away, and the old HIPAA regulations will be in effect unless HHS takes action or Congress takes some action to change the regulations around HIPAA and telehealth. Therefore, it is very important to know that this relaxation of the enforcement of HIPAA rules is temporary, and we should be prepared for it to change whenever the national emergency is over.
Basic Infrastructure
Remember, our goal is to protect the health information, wherever it is, and that information moves around the internet, just like email. The bad guys, the attackers, can live on any of the computers. They could live on your computer, the ones around the internet, like your internet service provider, or your remote patient's computer, and we have to protect all of the humans along the way. We need to ensure that everybody has the training they need, including our patients, to know how to protect their own devices because it also threatens their health information if their computers are not patched. You probably do not have control over their devices, but informed consent is something you can control, and you can tell the patient the risks and benefits of telehealth.
Install and Use Webcam Covers
Number one is a webcam cover. You almost certainly have a webcam if you are doing video-based telehealth and hacker’s notice. Hackers will sometimes use those cameras to spy on people, and having a cover that closes over the top of the webcam is an easy, cheap solution. Thus, whenever you are not using the webcam, be sure that the cover is closed so that even if a hacker has access to the computer, they cannot see what you are doing at the computer. The thing not to do is to put a post-it note over the camera. A piece of tape over the webcam is not a good cover. Stickers, tape, and post-it notes are ineffective at blocking what somebody can see through a camera. Get a real solid, legitimate webcam cover.
Selecting Telehealth Services
If you have access, or if you have responsibility for helping to select telehealth services, a couple of things to keep in mind. First, there are no special rules, no special laws in HIPAA devoted explicitly to telehealth. All HIPAA regulations apply to telehealth, but there are no special rules you need to follow. For example, make sure that you have the same security as you would for an in-person appointment. Only make sure that authorized users, for example, have access to electronic health information, whether physically and papers in your office or digitally during telehealth.
A couple of things to consider when you are looking for a telehealth provider or any technology solution for that matter, make sure the company you use will sign a business associate agreement. The business associate agreement is a way to mitigate risks that ensure that the provider will protect information when they have it on their computers. Make sure it has good encryption. If you do not know what that means, look for numbers like this, 256-bit AES, or numbers that are even bigger than that. It is suitable for telehealth to have a virtual waiting room so that you have to approve who is in that communication, and random strangers on the internet cannot just show up. It is nice to have good technical support, but that does not provide any security. It does not help protect the health information if they have 24/7 customer service, even though it is a nice feature.
Telehealth Checklist for Today
- Purchase and install a webcam cover
- Review/Update your Employee Handbook
- Review/Update your Notice of Privacy Practices q
- Create a Telehealth Consent Form for patients
- Confirm/Obtain a BAA with telehealth providers
- Install the latest updates for all software and devices q Update and run an antivirus scan
- https://designersecurity.com/TelehealthChecklist
If you want to download a longer list, I have made a telehealth checklist. These are things that you can do right away. You can go get a webcam cover. You can make sure that you have informed consent from patients and have the paperwork to back that up. This checklist can help you remember all of these things after the presentation.
Summary
Number one, you can protect yourself with trustworthy email and websites. We talked about a few ways to identify the red flags, what to look for, what to do if accidentally you click on a link or go to a website that could have been malicious. Not the end of the world, but that is one way hackers get access to our computers and health information. We want to be very careful about emails and websites. We talked about passwords and encryption, including how hackers get access to passwords. They guess the common passwords, and you probably do not want to use a common word password. It would be best if you thought about a password manager, maybe give that a try, and that would allow you to have strong passwords that you do not even have to remember. Remember to think like a criminal or think like a computer virus. You are all very good thinkers about healthcare security, and I have learned a lot in the pandemic about how PPE protects you and me and everybody from biological viruses.
In the same way, start to think a little bit about how digital threats impact you and the protections you can put in place to make sure that your computers are protected in the same way your physical health is. If you are looking for more information, there are some good reputable sources, and I put them here. I mentioned earlier that NIST is a good source and the British NCSC. It is never too late to try these things. We can always be more protected than we were, and it is a continual process, like we have to monitor our health all day, every day, so too do we have to make sure our digital devices are protected. The stakes are pretty high. I do not want criminals to have access to my health information, and so I very much hope that healthcare providers take it as seriously as you have.
Questions and Answers
How do I find someone to help me if I think I've been hacked?
That is a great question, it depends a little on your situation. If you have an IT organization at your business, that is a great first line of defense. They probably have seen or heard your question or your incident before, and they are the most knowledgeable to help mitigate it. If you are at home and you need some advice, the internet in one place if we have a little healthy skepticism. The government will play a role in some cyber incidents if they sort of meet a minimum threshold. And so yes, you can report to the FBI if you have been the victim of identity theft, for example, and they try to help as much as they can. If you get ransomware, for example, you can report that to the Department of Homeland Security. If you are looking just for general IT, there are vendors who offer this as a service. I am one of them, but you can search for example, for cyber security consulting and they might be able to help you with a single project, or you can retain them like other professional services, like an attorney or an accountant to help you on a continual basis.
Many of us are using more smartphones to communicate within our hospital or telehealth network, and share images or data. Should we be deleting data in the event our smartphones are breached or what do you recommend for storing data?
Sometimes we have to temporarily store sensitive data on our local device, whether it is a computer or a phone or a tablet. Encrypting the device is one protection against this, because even when that file is stored on the local device, it is still encrypted so that if the device is stolen, that information is not recoverable. One sort of technical thing that I will say is that when you just push the delete button on your computer to delete a file, the information is not actually erased. It still exists there even though you think it is gone. And so the digital device does not work the same as the physical world. There are some programs that you can download for what's called secure delete. I would especially encourage this when you are ready to get rid of a device. If you upgrade your phone, do not take the old phone and just give it to a friend or sell it on eBay or throw it into the dumpster. Get advice about how to securely erase all data to ensure there are no traces of photos, patient names, or other information.
Any antivirus recommendations, or go-to products, to help protect us at work or at home?
Antivirus is a really easy solution. It is relatively affordable, it does help protect from a lot of known threats. I encourage everybody on all their devices to have antivirus. There is no reason to say like, oh, well, Max does not get hacked, they do not need antivirus or... All devices are equally vulnerable and we need to protect them all. There are lots and lots of good antivirus. The names that I would feel very comfortable recommending them all, Symantec, McAfee, and Norton. Those vendors make very good products. I hear some people in healthcare say, well, they limit what I can do like they block the equipment that I need to use. I think that is not a reason to disable the antivirus, we can always find a way to make both work together because that is very important. I am generally less of a fan of free antivirus because like most things in life, we get what we pay for. The free products just are not updated as often, and they are not as robust as products we pay for when it comes to security. The other caveat I will give is I do not generally recommend an international company for antivirus products. Kaspersky, for example, is a Russian antivirus product. I'm sure they are very good, it is just not one that I personally recommend.
References
Hackers are stealing millions of medical records – and selling them on the dark web, CBS News, https://www.cbsnews.com/news/hackers-steal-medical-records-sell-them-on-dark-web/
Digital Identity Guidelines, NIST Special Publication 800-63B, https://pages.nist.gov/800-63-3/sp800- 63b.html
Information for Individuals & Families, UK National Cyber Security Centre, https://www.ncsc.gov.uk/section/information-for/individuals-families
How to secure, protect, and completely lock down your Android phone, PCWorld, https://www.pcworld.com/article/3332211/secure-android-phone.html
iOS 13: Security and privacy settings you need to tweak and check, ZDNet, https://www.zdnet.com/article/ios-13-security-and-privacy-settings-you-need-to-tweak-and-check/
LastPass Password Manager, https://lastpass.com/
Secrets and Lies: Digital Security in a Networked World, Bruce Schneier, 2015
Citation
Dykstra, J. (2021). Everyday cybersecurity best practices for respiratory. Continued.com - Respiratory Therapy, Article 121. Available at www.continued.com/respiratory-therapy
